A friend asked a question about looking at how Azure Storage Explorer makes its API calls to Azure using something like Fiddler.
The issue with just firing up Fiddler and watching traffic is that to decrypt HTTPS traffic fiddler installs a root certificate so that SSL is terminated in Fiddler first so that it can show you the decrypted payloads back and forth etc…
That is normally fine with apps that use the standard WinINET libraries etc… to make HTTPS calls (like chrome). However, Azure Storage Explorer an Electron app using NodeJS and doesnt use these. Node also handles root CAs a bit differently and a long story short is that it doesn’t by default trust Fiddlers Root Cert that it installs. This means that HTTPS calls fail with a “unable to verify the first certificate” error.
Setting up Fiddler
First you need to set up Fiddler to decypt HTTPS traffic. You do this in Fiddlers options under Tools > Options > HTTPS.
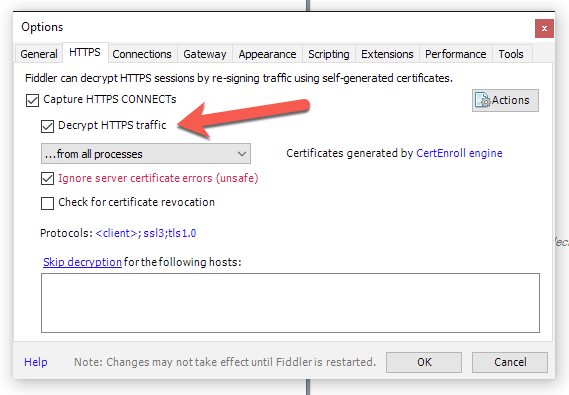
This will prompt you to install a certificate that Fiddler uses to terminate SSL in Fiddler so it can show you the decrypted traffic.
One You have completed this you need to export the certificate Fiddler installed so that you can set up Storage Explorer with it.
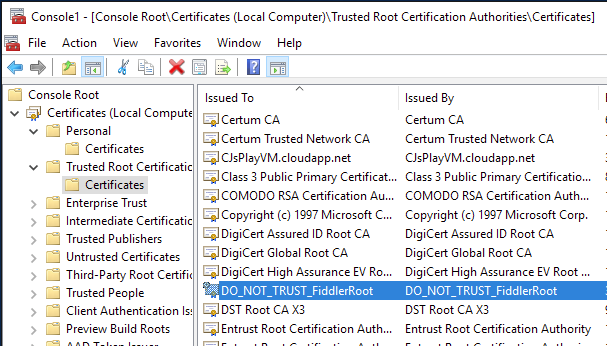
- Run MMC.exe
- File > Add Remove snap in
- Pick Certificates, when prompted choose “Computer account” and “Local computer”
- Navigate to Certificates > Trusted Root Certificates > Certificates
- Find “DO_NOT_TRUST_FiddlerRoot” certificate
- Right Click > All Tasks > Export
- As you go through the wizard choose “Base-64 encoded X.509 (.CER)” for the file format
- Save it your desktop or somewhere you will be able to find it later
Setting up Azure Storage Explorer
First up you need to configure Azure Storage Explorer to use Fiddler as a proxy. This is pretty straightforward.
In Storage Explorer go to the Edit -> Configure Proxy menu and add 127.0.0.1 and 8888 (fiddler defaults). Note: Not authentication should be used.
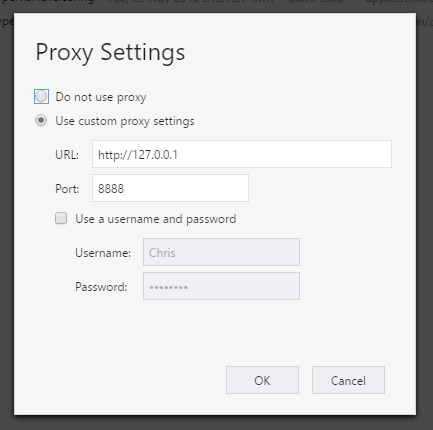
Now Storage Explorer will use Fiddler … however, you will start getting “unable to verify the first certificate” errors as Storage Explorer still doesnt trust the root certificate that fiddler is using for SSL termination.
To add the Fiddler certificate go to the Edit > SSL Certificates > Import Certificates. Pick the .cer file you saved out earlier. Storage Explorer will prompt you to restart in order for these to take effect.
Now when you start using Storage Explorer you should start seeing its traffic in Fiddler and in a readable decrypted state like below.
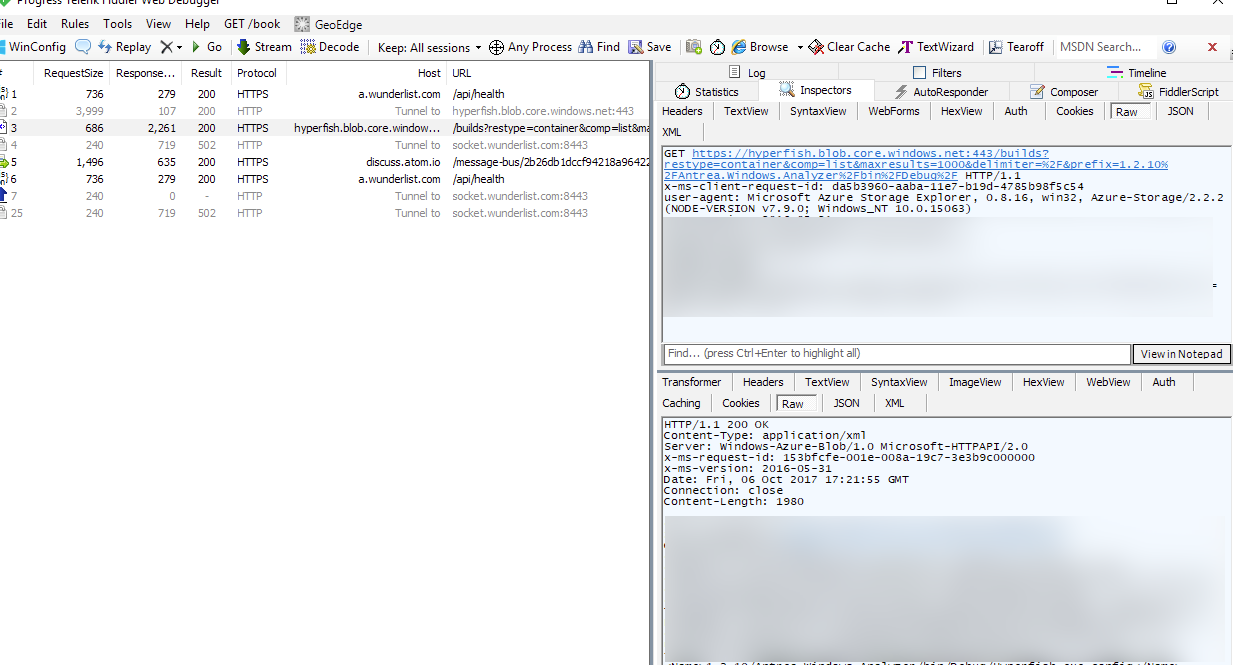
Now you can navigate around and do various operations and see what and how Azure Storage Explorer is doing it.
Happy Coding.
-CJ
Thanks Chris, it helped me 🙂
This is exactly what I was looking for. I am trying to work out the calls to ADLS Gen2.
Annoyingly, Gen2 Blob Containers don’t work. Everything else does though!
The specific error is in a dialog box:
[Window Title]
Microsoft Azure Storage Explorer
[Content]
Unable to retrieve child resources.
Details: write EPROTO 0:error:140770FC:SSL routines:SSL23_GET_SERVER_HELLO:unknown protocol:d:\buildagent\workspace\318698\vendor\node\deps\openssl\openssl\ssl\s23_clnt.c:827:
[OK]
I think this is something to do with Fiddler acting as the HTTPS proxy but not sure what is going wrong exactly.
Thank you!!!!